I have written before about both the good advances in technology, and the negative consequences of some of those developments. Here are a few more methods high tech methods that law enforcement uses, and occasionally misuses, in its investigations.
Stingrays
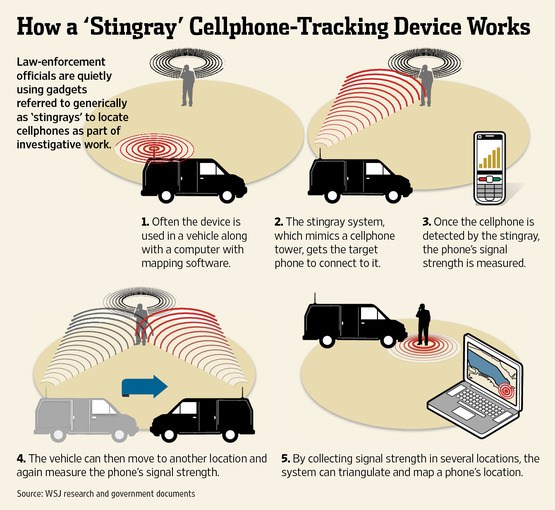
A Stingray is a brand of international mobile subscriber identity (IMSI) catcher, also known as a cell-site simulator. Each cellphone has an ISMI, a unique number usually comprising 15 digits that is stored in the SIM card. Stingrays are used by law enforcement and the military to locate individual cell phones by simulating or mimicking the strongest nearest cell site. The user’s phone connects to the Stingray because it offers the strongest signal. The IMSI catcher then maintains that signal connection until law enforcement tracks the location of the cell phone of the unsuspecting user. The use of such devices is highly secret and controversial because it is used without first obtaining a warrant from a judge, and rarely does the person or his attorney know that such a device was used. In addition, there is evidence that some of these devices can capture conversations or text messages which require judicial authorization.
Cell Phones

GPS Tracking
With a warrant, agents can place a GPS tracking device on a person’s car that records in real time the exact movements of the vehicle 24 hours a day, 7 days a week. Since police do not need to physically follow the vehicle, the person being surveilled remains completely unaware.
Facial Recognition
In 2014, the FBI’s Next Generation Identification (NGI) program became fully operational. The database contains almost 30 million photos. In addition, the FBI has access to some states’ driver’s license photos, State Department’s visa and passport database and the Department of Defense. 
Gunshot Detection
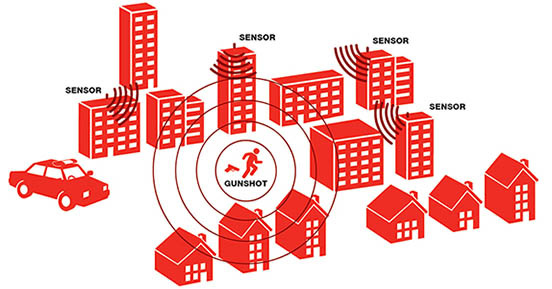
This technology uses a network of microphones to detect a gun’s unique explosive sound and then triangulates the source of the sound using GPS. Microphones are placed strategically around many cities and neighborhoods to capture the sound of gunshots and can even turn cameras toward the direction of the shots in an attempt to capture photos of the people involved. New York, Chicago and Washington D.C. have programs that identify and locate gunshots in real time.
Smart Home Devices
Smart home devices like Alexa, Amazon Echo and Google Home record not only a person’s requests and search history, they can also record ambient sounds in one’s home. Police have obtained warrants attempting to compel Amazon and others to turn over the recordings for murder investigations. 
Computers
Our computers and smart phones contain an unimaginable amount of personal information about our daily activities and lives. Law enforcement search and download suspects’ computers and phones daily in all type of investigations. 
Stahl Gasiorowski Criminal Defense Lawyers aggressively defend individuals charged with complex federal and state crimes. Founder Robert G. Stahl is recognized as one of the top criminal defense attorneys in the NY/NJ area for his skills, knowledge and success. To contact us to discuss your case, call 908.301.9001 for our NJ office and 212.755.3300 for our NYC office, or email us at rgs@sgdefenselaw.com



Leave A Comment